信息安全工程师当天每日一练试题地址:http://www.cnitpm.com/exam/ExamDay.aspx?t1=6
往期信息安全工程师每日一练试题汇总:http://www.cnitpm.com/class27-6-1.aspx
信息安全工程师每日一练试题(2017/9/26)在线测试:http://www.cnitpm.com/exam/ExamDay.aspx?t1=6&day=2017/9/26
信息安全工程师每日一练试题内容(2017/9/26)
试题
1: 当您发现因短信欺诈订制被扣除信息费时,可以向相关电信运营企业投诉;投诉未果,可进一步向申诉_____。
A、信息产业部或各地电信用户申诉受理中心(12300)
B、中国通信企业协会
C、中国互联网协会
试题解析与讨论:
http://www.cnitpm.com/st/2210513678.html试题参考答案:A
试题
2: 信息网络安全的第三个时代()
A、主机时代,专网时代,多网合一时代
B、主机时代,PC机时代,网络时代
C、PC机时代,网络时代,信息时代
D、2001年,2002年,2003年
试题解析与讨论:
http://www.cnitpm.com/st/2213921248.html试题参考答案:A
试题
3:
在图A-l 所示PKI 系统纬构中,负责生成和签署数字证书的是(1)负责验证用户身份的是(2 )
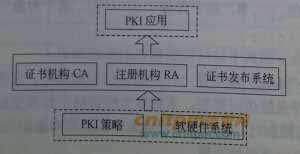
(1) A. 证书机构CA
B. 注册机构RA
C 证书发布系统
D. PKl 策略
(2) A. 证书机构CA
B. 注册机构RA
C 证书发布系统
D. PKl 策略
试题解析与讨论:
http://www.cnitpm.com/st/2300815016.html试题参考答案:A、B
试题
4:
以下关于网络流量监控的叙述中,不正确的是()
A、流量检测中所检测的流量通常采集自主机节点、服务器、路由器接口和路径等
B、数据采集探针是专门用于获取网络链路流量的硬件设备
C、流量监控能够有效实现对敏感数据的过滤
D、网络流量监控分析的基础是协议行为解析技术
试题解析与讨论:
http://www.cnitpm.com/st/2850711108.html试题参考答案:C
试题
5: In a contract with a hot, warm or cold site, contractual provisions should cover which of the following considerations?
A、Physical security measures
B、Total number of subscribers
C、Number of subscribers permitted to use a site at one time
D、References by other users
试题解析与讨论:
http://www.cnitpm.com/st/2929129138.html试题参考答案:C
试题
6: An IS auditor reviewing database controls discovered that changes to the database during normal working hours were handled through a standard set of procedures. However, changes made after normal hours required only an abbreviated number of steps. In this situation, which of the following would be considered an adequate set of compensating controls?
A、Allow changes to be made only with the DBA user account.
B、Make changes to the database after granting access to a normal user account.
C、Use the DBA user account to make changes, log the changes and review the change log the following day.
D、Use the normal user account to make changes, log the changes and review the change log the following day.
试题解析与讨论:
http://www.cnitpm.com/st/293402668.html试题参考答案:C
试题
7: Which of the following would be MOST important for an IS auditor to verify when conducting a business continuity audit?
A、Data backups are performed on a timely basis
B、A recovery site is contracted for and available as needed
C、Human safety procedures are in place
D、Insurance coverage is adequate and premiums are current
试题解析与讨论:
http://www.cnitpm.com/st/294816846.html试题参考答案:C
试题
8: With respect to business continuity strategies, an IS auditor interviews key stakeholders in an organization to determine whether they understand their roles and responsibilities. The IS auditor is attempting to evaluate the:
A、clarity and simplicity of the business continuity plans.
B、adequacy of the business continuity plans.
C、effectiveness of the business continuity plans.
D、ability of IS and end-user personnel to respond effectively in emergencies.
试题解析与讨论:
http://www.cnitpm.com/st/297884533.html试题参考答案:A
试题
9: 《计算机信息系统安全保护等级划分准则》(GB17859——1999)中规定了计算机系统安全保护能力的五个等级,其中要求对所有主体和客体进行自主和强制访问控制的是()
A.用户自助保护级
B.系统审计保护级
C.安全标记保护级
D.结构化保护级试题解析与讨论:
http://www.cnitpm.com/st/326885401.html试题参考答案:C
试题
10: 设在RSA的公钥密码体制中,用于为(e,n)=(7,55),则私钥d=()。
A. 8
B. 13
C. 23
D. 37
试题解析与讨论:
http://www.cnitpm.com/st/327521419.html试题参考答案:C
